Passkeys have definitely been mentioned recently if you’ve been following cybersecurity news. Google is already implementing them, and they could revolutionise how people secure the internet. But what exactly are passkeys? And how much more effective are they compared to the password logins we’ve been using for years?
What is a passkey?
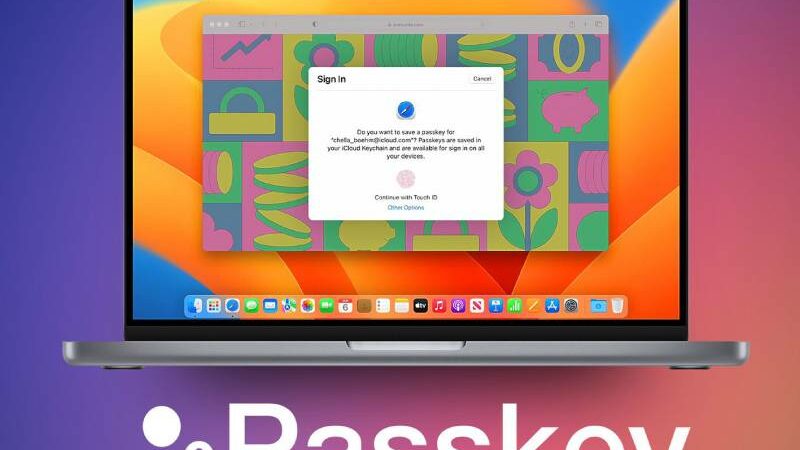
Passkeys are tied in with ditching password logins to stay away from their weaknesses (favoring those later). Instead, a pair of cryptographic keys are generated by an authenticator, such as a phone OS keychain or a separate password manager, which gives you access to other apps and websites. You actually need to confirm your personality through the authenticator, obviously, which likely means an expert secret word, with discretionary facial or unique mark acknowledgment to speed things up.
Portability is an essential feature of the passkey concept. As long as you have the master password to unlock things, it could be very simple to sync passkeys between your devices.
How does a passkey work?
Your authenticator generates a set of public and private cryptographic keys when passkeys are enabled in a website or application that is compatible with it. For secure verification, those keys are traded, encoding traffic against the rest of the world.
Public keys are called that since they’re put away on servers related with an application or site. A hacker might break into a server and get your key, but if you don’t have your master password and private key, it’s basically useless.
Private keys are constantly saved locally on your gadgets, and provided to servers just when something requests certifications. You need to check your personality for the interaction to finish. A server does not require all of a private key’s details because there is a mathematical link between it and its public counterpart.
Password versus passkey: Which is more protected?
Since passwords must inevitably be stored in a remote database, passkeys are generally more secure. Even though many businesses have security measures in place, a skilled hacker could break through them and use any logins they find immediately if they don’t have two-step verification (2SV). The situation gets worse when people use the same passwords too often. If the same password works on all servers, hackers won’t have to worry about it.
Human nature can overcome passwords in alternate ways. People frequently don’t give them enough thought, which makes it easy to guess or brute-force through repeated attempts. They occasionally share them with people we shouldn’t, such as those who have fallen for phishing scams, when that isn’t a problem.
Naturally, passkeys are not impenetrable. Assuming somebody snags one of your authenticators and your lord secret word, they might have the keys to your whole computerized life, or least all that utilizes a passkey. However, that ought to be less likely than attacks on remote servers.